A new form of digital identity theft is circumventing the security measures designed to stop its predecessor. Being named SIM Swap 2.0 by cybersecurity researchers, this advanced SIM hijacking method eliminates the need for physical SIM card replacement or social engineering of mobile carrier staff. This technique allows attackers to intercept one-time passwords (OTPs) and compromise high-value accounts with chilling efficiency. The threat poses a severe and escalating risk to cryptocurrency exchanges, fintech platforms, and any service relying on SMS-based multi-factor authentication (MFA)
The Evolution from Classic SIM Swap to SIM Swap 2.0
The classic SIM swap was a blunt instrument relying on social engineering. This method enable the attacker to instantly transferred the victim’s number, enabling a multi-factor authentication breach by intercepting SMS OTPs to hijack email, financial, and cryptocurrency accounts. SIM Swap 2.0 is a more advanced SIM hijacking method that bypasses human interaction entirely. The victim’s SIM remains active and never lose service. The attacker exploits the SS7 and SIP-based routing infrastructure, targeting the telecom routing vulnerability to silently reroute a number’s communications.
How SIM Swap 2.0 WorksTechnically?
The term “SIM Swap 2.0” is a misnomer, but it has stuck due to the similar end result. It is more accurately described as a mobile number rerouting fraud or a digital identity takeover attack facilitated by manipulating the rules that govern how telephone numbers are reached across network boundaries. The entire process is designed to be a silent SIM hijack flow, leaving the victim unaware until it is too late. The attack can be broken down into five distinct, technical phases:
Reconnaissance and VoIP Endpoint Establishment.
The attacker begins by identifying a high-value target, often through data breaches related to cryptocurrency exchanges or by scanning professional social networks like LinkedIn for individuals in the fintech or blockchain space. Simultaneously, they acquire an account with a VoIP service provider. These providers vary widely in their security postures; some smaller or less-regulated operators have minimal user identity validation issues, allowing accounts to be set up with stolen or synthetic identities. This VoIP account becomes the malicious endpoint, the destination for the victim’s rerouted communications.
The Number Rerouting Manipulation.
This is the core of the exploit. The attacker submits a request to the telephony routing ecosystem indicating that the victim’s number should now be “hosted” on their controlled VoIP network. This can be achieved by exploiting insecure administrative portals or APIs used by smaller telecoms and VoIP carriers, using compromised credentials of telecom employees, or submitting a spoofed identity request to a number portability clearinghouse. The request creates a backend routing anomaly, effectively telling the global telephone network, “This number has moved; send all its inbound traffic to my server.”
The Unauthorized Network Handoff.
Once the fraudulent routing update propagates, the silent SIM hijack flow is activated. The victim’s phone remains connected to their legitimate mobile carrier and can likely still make outbound calls and send SMS. However, all inbound communications including the critical SMS OTPs are secretly handed off to the attacker’s VoIP endpoint. This unauthorized network handoff is the exploit’s superpower: it compromises security without triggering the obvious “no service” alert that a traditional SIM swap causes.
OTP Relay Interception and Account Takeover.
With the rerouting active, the attacker springs into action. They visit the target’s cryptocurrency exchange, bank, or email provider, click “Forgot Password,” and request a login code via SMS. The service sends the code, and due to the manipulated routing, it is delivered to the attacker’s controlled VoIP environment. This SMS OTP bypass via VoIP is a direct MFA security gap. The attacker uses this intercepted code, along with other previously breached credentials, to gain full access. This process of capturing and using the code in real-time is known as OTP relay interception.
Asset Extraction and Covering Tracks.
The final phase is the theft. In the case of a crypto wallet takeover attempt, the attacker will quickly transfer assets to their own wallets, often using mixers or chain-hopping to obfuscate the trail. For bank accounts, they may initiate wire transfers or add new, controlled devices for authentication. Following the theft, the attacker often reverts the routing changes or simply abandons the burner VoIP account, making forensic investigation significantly more difficult.
Abusing VoIP Number Routing and Interconnection
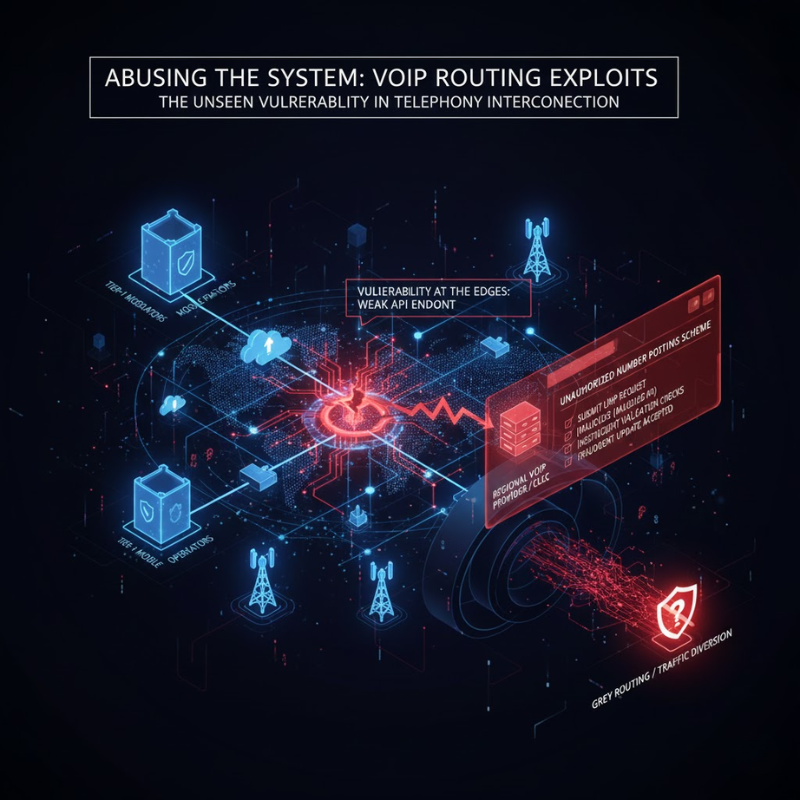
The viability of SIM Swap 2.0 hinges on exploiting the complex interconnection between telecom and VoIP networks. The telecom routing vulnerability often lies with smaller VoIP providers whose administrative portals or APIs lack robust authentication. Attackers exploit these weak points to submit fraudulent local number portability requests. If validation fails, this unauthorized number porting scheme is accepted then reroute the victim’s number without a legitimate carrier transfer. This manipulation sometimes concealed via grey routing. It creates a backend routing anomaly that diverts traffic to the attacker, severely complicating the incident response workflow for investigators.
Primary Targets and the Crypto Connection
The targets of SIM Swap 2.0 are not random; they are selected for maximum financial return. The attack pattern consistently zeroes in on sectors where high-value assets are protected by a single, fallible SMS OTP.
The Cryptocurrency Landscape
The crypto OTP interception technique is devastatingly effective because many major exchanges still use SMS as a primary or backup 2FA method. A successful VoIP-based SIM swap attack gives attackers direct access to trading accounts. The unauthorized withdrawal attempt flags may be triggered, but by the time the user sees the alert email or the exchange’s security team reviews the activity, the assets are often already gone. The pseudonymous and irreversible nature of blockchain transactions creates severe transaction reversal challenges, making recovery a rare exception.
High-Finance Fintech and Traditional Banking
PayPal, Venmo, and Chime are also prime targets. An attacker can link stolen bank accounts to these platforms for rapid fund movement or take over the accounts directly. The VoIP-enabled MFA compromise provides a direct path to initiating wire transfers or changing linked bank accounts.
The Central Hub : Email Accounts
A compromise of a primary email account, especially one tied to a recovery address for other services, is a catastrophic event. It allows an attacker to perform unauthorized authentication resets across a victim’s entire digital life, from Amazon to Apple iCloud, compounding the damage exponentially.
These attacks are frequently executed during off-hours, late on Friday nights or over holiday weekends. This strategic timing delays the victim’s detection, because they are usually not actively using their phone, giving the attacker a critical head start.
Early Indicators of a Compromise
Unlike a traditional SIM swap where service drops abruptly, the signs of a SIM Swap 2.0 attack are more nuanced. Users and corporate security systems must be educated to recognize these red flags:
Unexpected Authentication Requests
Receiving an SMS OTP or a push notification from an authenticator app for a service you are not currently accessing is one of the strongest early indicators.
Service Disruptions
Inbound calls from certain carriers or locations might go directly to voicemail or fail to connect entirely. There may be a noticeable delay of several minutes in receiving expected SMS messages from services or contacts.
Digital Breadcrumbs
Emails from service providers notifying of a login from a new device, a password change, or a new 2FA method being added. It’s all initiated by the attacker.
Suspicious Voicemails
Finding voicemails from automated systems that read out numeric codes (e.g., “Your verification code is 1-2-3-4-5-6”).
Carrier Notifications
While less common in pure routing attacks, some carriers may send a generic SMS or email notification about a change to account settings, call forwarding, or a “port request” that the user did not initiate.
Why Do These Attacks Succeed and Go Unnoticed?

The persistence of SIM Swap 2.0 is not due to a single point of failure but a cascade of systemic and technical gaps across the telecommunication industry.
The API Security Gap
The modern telephony network runs on APIs. The digital authentication loophole often exists because the APIs responsible for number porting and routing at smaller providers are not subjected to the same rigorous security testing, rate-limiting, and monitoring as customer-facing applications. They are “back-office” systems, historically trusted within a closed ecosystem, now exposed to global threat actors.
The Identity Verification Chasm
The security standard for verifying a number transfer request varies wildly. A tier-1 mobile operator may require a PIN and multiple data points, while a smaller VoIP provider might only require an account number and a readily available piece of PII. This inconsistency creates a weak link that attackers systematically seek out and exploit.
The Coordination and Monitoring Deficit
The sheer number of interconnected networks makes it nearly impossible to maintain a unified, real-time view of anomalous routing changes. There is no global “kill switch” or centralized audit log for telephony routing. A fraudulent update can slip through the cracks of one provider and propagate before real-time fraud detection systems at another provider can flag it as anomalous. This lack of a coordinated security monitoring escalation protocol is a critical enabler for these attacks.
The Impact Beyond Immediate Financial Loss
The immediate financial devastation of a drained cryptocurrency wallet or bank account is the most visible impact. However, the long-term consequences of a successful digital identity takeover attack are often more profound and lingering.
Permanent Loss of Digital Assets
As mentioned, the irreversible nature of most cryptocurrency transactions means that stolen funds are almost never recovered. Victims can be left with no recourse, turning a digital asset into a total loss.
The Long Tail of Identity Theft
Regaining control of a hijacked email account can take days or weeks, during which the attacker can reset passwords for other linked accounts, apply for credit, or impersonate the victim for further fraud. The user identity validation issues that allowed the initial attack can hamper the victim’s own recovery efforts, as they struggle to prove their identity to service provider help desks.
Psychological and Reputational Damage
The violation of having one’s digital identity hijacked carries a significant psychological toll. Victims report feelings of anxiety, vulnerability, and a loss of trust in the digital ecosystems they rely on for their professional and personal lives. For business professionals, a compromised social media or email account can lead to reputational harm with clients and colleagues.
Data, Trends, and Analytical Findings
While the exact scale of SIM Swap 2.0 is hard to measure, industry data confirms a sharp rise. The Crime Complaint Center (IC3) has warned of evolving SIM swap schemes and a 2024 cloud-security report noted a 150% year-over-year increase in telephony fraud, with VoIP-based SIM swap attacks being a key driver. This growth is fueled by a burgeoning underground marketplace where automated attack scripts are sold, commoditizing the advanced SIM hijacking method and enabling a broader range of criminals to execute these digital identity takeover attacks.
How Perpetrators Cover Their Tracks
The operational security (OpSec) of these attackers is sophisticated, designed to create multiple layers of obfuscation between the crime and the criminal.
Infrastructure Laundering
Attackers use burner VoIP accounts registered with stolen identities and pre-paid credit cards. They chain multiple VoIP providers together, creating a maze of unauthorized network handoffs that forensic analysts must unravel.
Geographic Obscurity
The attacks are routed through Virtual Private Servers (VPS) and proxy networks located in jurisdictions with weak law enforcement cooperation, making attribution exceptionally difficult.
Automation and Speed
The use of automated attack scripts allows for the entire process from triggering the routing change to executing the password resets and asset transfers, to be completed in a matter of minutes. This speed minimizes the window for detection and intervention by any real-time fraud detection systems that may be in place.
Prevention and Mitigation for Users and Institutions
Combating SIM Swap 2.0 requires a fundamental shift away from treating a phone number as a secure identity token. A layered defense strategy is essential.
For Individual User
Eliminate SMS-Based 2FA
The single most important action is to disable SMS for two-factor authentication on every account that offers a more secure alternative. Migrate to hardware security keys (e.g., YubiKey) which are phishing-resistant, or use a time-based OTP application (like Google Authenticator or Authy). These are immune to SMS OTP bypass via VoIP.
Use Advanced Account Security Features
On cryptocurrency exchanges, enable all available security features: whitelisting of withdrawal addresses, mandatory 24-48 hour delay on withdrawals, and transaction email confirmations. For email and cloud accounts, use biometric logins and hardware keys.
Implement Carrier Protections
Contact your mobile provider and place a “SIM Lock,” “Number Lock,” or “Port Freeze” on your account. This adds an extra layer of verification, typically a unique PIN code, that must be provided before any number porting request is processed. It is a crucial barrier, though not impervious to all unauthorized number porting schemes.
Practice Digital Hygiene
Use a unique, strong password for your primary email account and mobile carrier account. Consider using a separate Google Voice or landline number for account recovery that is not widely publicized.
For Institutions (Exchanges, Banks, Email Providers)
Deprecate SMS 2FA
Actively discourage or phase out SMS as a 2FA method for high-risk actions, pushing users toward more secure alternatives.
Enhance Behavioral Analytics
Implement sophisticated real-time fraud detection systems that can flag logins from new devices combined with rapid-fire password reset requests and withdrawals, freezing activity until manual review by a security team.
Strengthen User Verification
For high-value transactions and account recovery, move beyond knowledge-based questions to more robust user verification enhancement processes.
How The Regulatory and Industry Response
In response to the escalating threat, regulators and industry consortia are beginning to take action, though the pace is often slower than that of the attackers.
The FCC and Telecom Regulation
The Federal Communications Commission (FCC) has released new rules aimed at strengthening identity protection policies for phone customers. These rules require carriers to adopt secure methods of authenticating a customer before redirecting a number and to provide immediate notification to customers when a SIM change or port request is made. However, these rules are primarily aimed at the traditional SIM swap model and are still being adapted to address pure routing exploits.
Industry-Led Initiatives
Groups like the Alliance for Telecommunications Industry Solutions (ATIS) are working on best practices and technical standards to secure the routing ecosystem. This includes promoting stricter API security standards, mandatory audits of routing databases, and improved information sharing between carriers about fraudulent activity and backend routing anomalies.
Provider Accountability
There is growing pressure on VoIP providers to tighten their onboarding and number administration processes. This includes implementing more rigorous identity protection policies and participating in industry-wide security monitoring escalation programs to quickly identify and shut down bad actors abusing their platforms.
Conclusion: An Evolving Battle in the Shadows
SIM Swap 2.0 represents a significant and worrying evolution in the digital threat landscape. It shifts the battlefield from the mobile carrier’s retail storefront and call center to the obscure, technical plumbing of global telephony routing. This VoIP-enabled MFA compromise demonstrates a stark reality: as defenses harden around one vulnerability, determined threat actors will innovate and find another, often in the complex, interconnected systems that underpin our digital lives. Regulators need to update frameworks to encompass these technical exploits. Service providers must urgently guide users away from SMS-based authentication. For individuals, the era of trusting a phone number as a secure anchor for their digital identity is over.
Publisher’s Disclaimer and Educational Purpose
MEXQuick publishes this educational resource for informational and awareness purposes only. The content is based on analysis of publicly available threat intelligence and official guidance from established cybersecurity authorities. We are an independent publisher and are not affiliated, associated, authorized, endorsed by, or in any way officially connected with any subsidiaries or affiliates. All brand names and trademarks mentioned are the property of their respective owners.
This article is intended to provide general guidance and should not be interpreted as professional, technical, or legal advice. While we strive for accuracy, the dynamic nature of cyber threats means that specific tactics may evolve. Readers are strongly encouraged to verify any information directly through the official sources linked within this article. The primary goal of this content is public education and phishing awareness, and MEXQuick assumes no responsibility for any individual actions taken based upon the information provided herein.
